The OWASP Top 10 is a technical document that summarizes the most critical risks to web application security worldwide.
It is built using data from hundreds of thousands of applications, contributed by multiple security vendors and the OWASP community.
It is not a legal standard, but rather a model and baseline that developers, CISOs, and cybersecurity teams can use to prioritize their efforts.
Since its first publication, OWASP has consolidated the Top 10 as a practical guide for both technical teams and business leaders. Historically, the document has been updated in 2003, 2004, 2007, 2010, 2013, 2017, 2021, and now 2025, becoming a reliable thermometer of the real threats affecting web applications over time.
OWASP currently aims to maintain an update cycle of approximately 3 to 4 years, a deliberate balance between stability and relevance. This approach ensures that the Top 10 remains a solid foundation for security policies, training programs, audits, and compliance, without falling behind the rapid evolution of attack techniques and new exposure surfaces.
Benefits of the OWASP Top 10
The creation process of the OWASP Top 10 relies on a combination of empirical data and practical experience. Millions of results from automated scans, penetration tests, bug bounty programs, and real security incident reports are analyzed. This is complemented by direct contributions from the global security community, which provides context, validation, and expert judgment.
Key benefits include:
✔️ Aligns the entire organization (developers, system administrators, security, business) around a common language about critical cybersecurity risks.
✔️ Serves as a minimum checklist for security requirements in SDLC, testing, audits, and compliance (clients often request “no critical OWASP Top 10 findings”)..
✔️ Helps prioritize. Instead of trying to cover “everything,” it focuses first on what generates the most real-world impact based on global data.
✔️ It is free, open, and maintained by a global community, making it especially valuable for small and medium-sized companies.
Typical example: A fintech adopts the OWASP Top 10 as a baseline list of requirements in user stories, security acceptance criteria, and pentesting before going live.
New Version: “OWASP Top 10 2025”
The OWASP Top 10 2025 represents the latest edition of the world’s leading reference standard for the 10 most critical risks in web application security. This update aims to more accurately reflect how modern applications are built, deployed, and attacked in 2025, in a context shaped by cloud architectures, microservices, exposed APIs, automation, artificial intelligence, and increasingly accelerated development cycles.
Thanks to this approach, the Top 10 is not a static list. Each edition adjusts rankings, merges categories when attack vectors converge, and incorporates new threats when real-world trends demand it. The result is a living document aligned with how applications are compromised today and with the risks that truly generate technical, operational, and reputational impact for organizations.
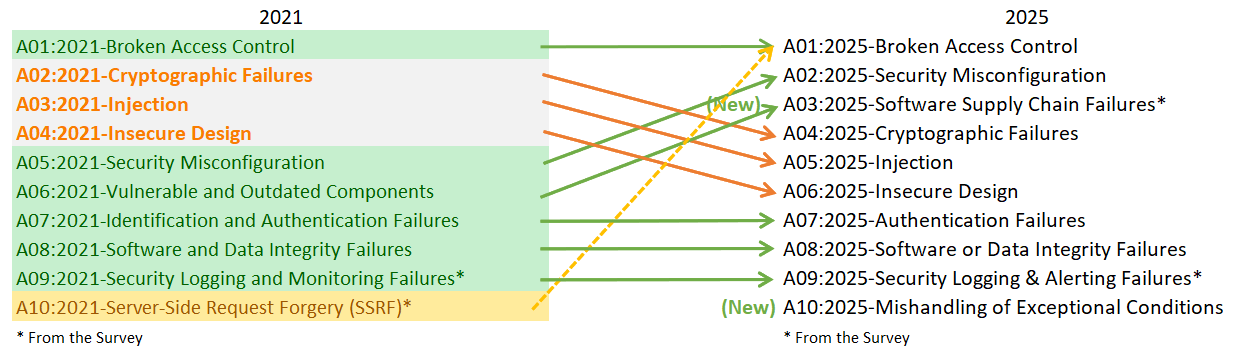
The 2025 list (RC version), unlike the 2021 edition, includes:
A01: Broken Access Control.
A02: Security Misconfiguration.
A03: Software Supply Chain Failures.
A04: Cryptographic Failures.
A05: Injection.
A06: Insecure Design.
A07: Authentication Failures.
A08: Software or Data Integrity Failures.
A09: Logging & Alerting Failures.
A10: Mishandling of Exceptional Conditions.
Source image: https://owasp.org/Top10/2025/0x00_2025-Introduction/
A01 – Broken Access Control (still #1)
▪️It remains in the top position because virtually all analyzed applications show some form of access control failure (3.7% average incidence, 40 mapped CWEs).
▪️OWASP explicitly states that this continues to be the most serious risk because many organizations still fail to implement a robust, centralized, and contextual authorization model.
▪️This category consolidates CWEs such as information exposure and also SSRF (CWE-918), absorbing part of what used to be A10 in 2021.
A02 – Security Misconfiguration (rises in importance)
▪️It moves to A02 because data shows a high incidence of configuration errors in cloud environments, containers, proxies, WAFs, buckets, etc.
▪️The change reflects that exploiting a misconfiguration is often easier and more profitable for an attacker than finding a complex zero-day.
▪️Organizations are automating deployments (IaC, pipelines), and any flawed template, role, or policy gets replicated massively, increasing the impact of this category.
A03 – Software Supply Chain Failures (new category)
▪️New in 2025, it expands the 2021 category “Vulnerable and Outdated Components,” but now covers the entire chain: dependencies, repositories, builds, CI/CD, and distribution.
▪️It was created because supply chain attacks (malicious packages, compromised repos, poisoned container images, backdoored pipelines) have become one of the most critical attack vectors.
▪️OWASP gives it its own category to force organizations to see this as a systemic problem, not just “I have an outdated library.”.
A04 – Cryptographic Failures (drops slightly in ranking)
▪️It remains in the list but below “Software Supply Chain Failures” because frameworks and managed services have improved cryptographic defaults (TLS, storage, hashing).
▪️Even so, data shows a significant volume of errors: insecure protocols, weak keys, lack of encryption at rest or in transit.
▪️OWASP keeps this category because cryptographic failures remain devastating, but acknowledges that other issues are causing more new incidents in practice.
A05 – Injection (drops relative to other risks)
▪️Injection drops in ranking not because it has disappeared, but because the widespread use of ORMs, frameworks, and validation has significantly reduced its prevalence in new applications.
▪️Testing still finds injections (SQL, NoSQL, OS, LDAP, etc.), but many can be mitigated with well-known standard controls.
▪️OWASP reorders the list to reflect that today, in terms of “novelty” and emerging risk, “Security Misconfiguration” and “Software Supply Chain Failures” weigh more than classic injections.
A06 – Insecure Design (drops in position but not in importance)
▪️It drops slightly, but the official message is that insecure design remains a root cause behind almost all other categories.
▪️It focuses on issues that are not simple implementation bugs but architectural decisions: missing threat models, lack of domain separation, business logic flows that can be abused.
▪️OWASP keeps the category because without good design, technical mitigations are just patches; it simply adjusts its relative position compared to more quantifiable risks like misconfigurations or supply chain issues.
A07 – Authentication Failures (adjusted, same focus)
▪️This is the evolution of the 2021 “Identification and Authentication Failures,” updated to focus on MFA, sessions, tokens, federation, and modern login flows.
▪️Its position reflects that many incidents still begin with weak credentials, hijacked sessions, misconfigured MFA, or authentication flow bypasses.
▪️It does not rise to the top 3 because the combined impact of misconfigurations and supply chain issues is proving more critical at scale, but it remains fundamental.
A08 – Software or Data Integrity Failures (maintained and reinforced)
▪️It maintains the essence of 2021, focusing on code and data integrity (signatures, software updates, repositories, insecure serialization).
▪️It differs from A03 in that A03 focuses on the entire ecosystem and supply chain, while A08 focuses on ensuring that what is executed and stored has not been tampered with.
▪️It remains its own category because integrity failures enable large-scale attacks even when there is no “classic vulnerability,” but rather an abuse of trust.
A09 – Logging & Alerting Failures (slight adjustment)
▪️It evolves from “Security Logging and Monitoring Failures” to emphasize that it is not only about logging but also about alerting and detecting effectively.
▪️OWASP keeps it because many incidents worsen due to lack of adequate traces or actionable alerts, hindering response and forensics.
▪️The ranking indicates that although it is key for detection and response, other categories carry more weight in the attacker’s initial vector.
A10 – Mishandling of Exceptional Conditions (brand new category)
▪️New in 2025, it groups issues related to incorrect handling of exceptions, errors, timeouts, resource failures, edge cases, etc.
▪️OWASP notes that many breaches and resilience failures stem from how the application behaves when something goes wrong: errors exposing data, failures leaving inconsistent states, “fail-open” behaviors bypassing controls.
▪️Previously, these issues were scattered across “quality” CWEs, but now they are elevated to a security category to reflect that software must fail safely, not just work well in the “happy path.”
Summary Table: OWASP Top 10 2021 vs 2025
| Year | Rank | Category | Situation in 2025 |
| 2021 | A01 | Broken Access Control | Remains A01, same focus. |
| 2021 | A02 | Cryptographic Failures | Drops to A04. |
| 2021 | A03 | Injection | Drops to A05. |
| 2021 | A04 | Insecure Design | Drops to A06. |
| 2021 | A05 | Security Misconfiguration | Rises to A02. |
| 2021 | A06 | Vulnerable and Outdated Components | Expands into A03 Software Supply Chain Failures. |
| 2021 | A07 | Identification and Authentication Failures | Renamed as A07 Authentication Failures. |
| 2021 | A08 | Software and Data Integrity Failures | Evolves into A08 Software or Data Integrity Failures. |
| 2021 | A09 | Security Logging and Monitoring Failures | Becomes A09 Logging & Alerting Failures. |
| 2021 | A010 | Server-Side Request Forgery (SSRF) | Consolidated into other categories (e.g., A01). |
| 2025 | A010 | Mishandling of Exceptional Conditions | New category in 2025. |
Underlying Reasons for Periodic Changes
The reordering of the OWASP Top 10 2025 is not arbitrary. It responds to deep changes in how software is built, deployed, and attacked today.
First, technology has changed. The massive adoption of public cloud, containers, microservices, exposed APIs, CI/CD pipelines, complex supply chains, and even artificial intelligence has introduced new attack vectors that simply did not exist—or were not relevant—in editions like 2010 or 2013. Today’s exposure surface is broader, more distributed, and more dynamic.
The attacker profile has also changed. Instead of focusing solely on isolated technical vulnerabilities, attackers now prioritize more efficient and scalable attacks, such as supply chain compromise, abuse of excessive access resulting from poor role design, misconfigurations propagated through automation, and resilience failures that allow control bypass when systems enter unexpected states.
Finally, industry maturity has evolved. Issues that once dominated the landscape now have well-known controls, clear guidance, and default support in modern frameworks, reducing their prominence. In their place, more complex and systemic risks emerge, requiring new levels of attention, governance, and security-by-design.
According to OWASP, the Top 10 should be understood as a global baseline, a common reference for the entire industry. However, each organization should build and maintain its own internal “Top N,” tailored to its context, architecture, and threat model, and review it more frequently to avoid falling behind in a constantly evolving risk environment.
How Does OWASP Decide Which Categories Rise or Fall?
The decision-making process behind the OWASP Top 10 is not purely automatic or solely based on statistics. The project itself defines it as “data informed, but not blindly data driven.” This means that although it relies on large volumes of data from security testing, CVE reports, CWE mappings, and automated tools, these data points are not the only criteria.
In the first phase, OWASP analyzes and ranks around 12 candidate categories using metrics such as frequency, prevalence, and observed impact. However, the process does not end there. Space is explicitly reserved for at least two categories to be promoted by the community, even if quantitative data does not yet show a clear spike in scan results or public repositories.
This approach exists for a key reason: data always looks to the past. Statistics show what has already happened, but not necessarily what is emerging. Therefore, OWASP complements the analysis with a global survey of practitioners—pentesters, AppSec teams, security architects—who experience real attacks daily and detect patterns before they become widespread or easily measurable.
The direct consequence of this model is important: a category may rise, fall, or even enter as new, even if it is not the one with the highest absolute number of vulnerabilities. If the community perceives it as critical, strategic, or with high future impact potential, OWASP gives it visibility to anticipate the problem rather than react too late.
This balance between historical data and expert judgment keeps the OWASP Top 10 a living, relevant reference aligned with the operational reality of modern application security.
In this context, the OWASP Top 10 2025 delivers a clear message: web security is no longer determined solely by a poorly written line of code, but by design decisions, configurations, dependencies, and how applications react when something goes wrong. Understanding this evolution is not just a technical matter, but a strategic one.
If your goal is to evaluate the real security of your applications according to the OWASP Top 10 2025, at Internet Security Auditors we perform updated web pentesting focused on the risks that are currently causing real incidents, such as access control, cloud configurations, supply chain, insecure design, and resilience failures, among others.
Our services go beyond running scanners or checking boxes: we analyze applications as a real adversary would, aligning each finding with OWASP, business impact, and clear technical mitigation recommendations.

